Click tabs and you’ll find here activity guides links video quiz game about the topic
What is hacking?
Hacking is when someone breaks into a computer system. They usually do this by targeting people using email and website scams or malware, a software that can damage your device or let a hacker in.
From banking to shopping, and streaming to social media, people are spending more time than ever online. This means more opportunities for hackers to carry out cyber-attacks.
If hackers get into your device or accounts, they could access your money and personal information and you could become a victim of identity theft or identity fraud. Identity theft is when your personal details are stolen and identity fraud is when those details are used to commit fraud.
Identity theft happens when hackers can gather enough information about someone’s identity, like their name, date of birth, current or previous addresses and use this to carry out identity fraud. If you’re a victim of identity theft, it can have a direct affect on anything from your social media and email accounts to your personal finances, and could also make it difficult for you to get things like loans, credit cards or a mortgage until the problem is resolved.
Identity fraud is when the hackers who have stolen your identity use it in criminal activity to get products or services while lying about their identity. This can be really serious, hackers can use your identity details to open bank accounts, get credit cards, order products in your name, take over existing accounts and take out mobile phone contracts. Hackers could even get genuine documents such as passports and driving licenses in your name once they have stolen your identity. The act of stealing an person’s identity details is not identity fraud, but using that identity for any of the activities listed does.
Often the first sign that you have been a victim of identity theft or identity fraud may be when you receive bills for things you haven’t ordered or when you receive letters from debt collectors for debts that aren’t yours. This is why its so important to take actions to protect yourself from getting hacked in the first place.
Reference:
“Internet Safety: How to Protect Yourself against Hackers.” How to Protect Yourself Against Hackers | The Office of Attorney General Keith Ellison, https://www.ag.state.mn.us/consumer/publications/HowtoProtectYourselfAgainstHackers.asp.
How to protect yourself from hackers
Keep your passwords safe
If a hacker gets into your email, they could reset your other account passwords and access information you have saved about yourself or your business. Your email password should be strong and different to all your other passwords. This will make it harder to crack or guess.
- Using 3 random words is a good way to create a strong, unique password that you will remember. You should also protect your other important accounts, such as banking or social media.
- Saving your password in your browser means letting your web browser (such as Chrome, Safari or Edge) remember your password for you. This can help make sure you do not lose or forget your passwords and protect you against some cyber crime, such as fake websites. It is safer than using weak passwords, or using the same password in more than one place.
- Two-factor authentication (2FA) helps to stop hackers from getting into your accounts, even if they have your password. Some online banking uses 2FA automatically. It does this by asking for more information to prove your identity, such as a code that gets sent to your phone.
Think before you post
Are you ok with uploading or sharing something your parents, carers, teachers, or future employers might see? Once you post something, you lose control of it, especially if someone else screenshots or shares it. Keep things like your address, phone number, full name, school and date of birth private, and check what people can see in your privacy settings. Remember that people can use small clues like a school logo in a photo to find out a lot about you.
We have information on how to stay safe and update your privacy settings on Facebook, Instagram, TikTok, Snapchat and Twitter, so you can decide who is able to view what you post.
Have a listen to our Young Scotcast here or by pressing play below and hear Capital’s Katy J finding out just how much information Declan Doyle, Head of Ethical Hacking at the Scottish Business Resilience Centre, can find about her online.

What is ethical hacking?
Do You Think You Have Something Valuable To Steal?
What Are The Chances You Will Get Hacked?
Activity1:
Youtube Simulator HACKED, a project made by Thankful Box using Tynker. Learn to code and make your own app or game in minutes.
Activity2:
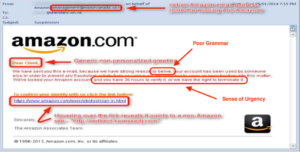
Notes:
- Generic greeting – This email has a generic greeting and does not address the recipient by name.
- Incorrect company information – This email address is missing an “A”, so is clearly not from an Amazon employee. Also, the link reveals that it points to a non-Amazon site, which should not be the case if this was a legitimate email from Amazon.
- Sense of urgency – The email is stating that the user needs to click a link in the next 36 hours or else their Amazon account will be terminated.
- Poor grammar – The grammar in this email is not professional. The misspelling of “believe” should be a red flag.
Watch this:—-> https://youtu.be/vheFIrl1LAs?t=33





