Click tabs and you’ll find here activity guides links video quiz game about the topic
How to Use Email Safely
Email has become an integral form of communication for kids, teens, and adults alike. Statista reports that 90% of individuals ages 15-24 use email as of 2019. Kids use it to register for accounts and communicate with friends; teens do the same, but they also use it to apply for colleges, scholarships and jobs.
E-mail Basic:learn how to use common email features and practice proper etiquette.
Email is a wonderful tool for sending and receiving a lot of information quickly and securely. However, it’s important that your personal information remains secure and safe and that you aren’t open to viruses or hackers.
Here are some safety tips when using email:
- Change your password regularly and keep it in a safe place.
- Don’t share your password with anyone.
- Don’t open attachments from anyone you don’t know.
- Log out or sign off from your account when you’ve finished looking at/sending your email.
- Don’t reply to spam or forward chain emails.
- Keep your personal information personal – don’t share bank or credit card information by email.
- Your bank will not discuss your private financial situation by email. If you receive any correspondence that claims to come from your bank, telephone your branch to verify it and discuss the matter over the telephone instead.
- Make sure that you have antivirus software installed and keep it up to date.
- Look out for malicious emails (they may look like they have come from a financial institution, an e-commerce site, a government agency or any other service or business)
- Enable filters on your email programs and report spam
- Pay attention to the website’s URL
Examples of Phishing Emails
Here are a few examples of phishing emails that we’ve received:
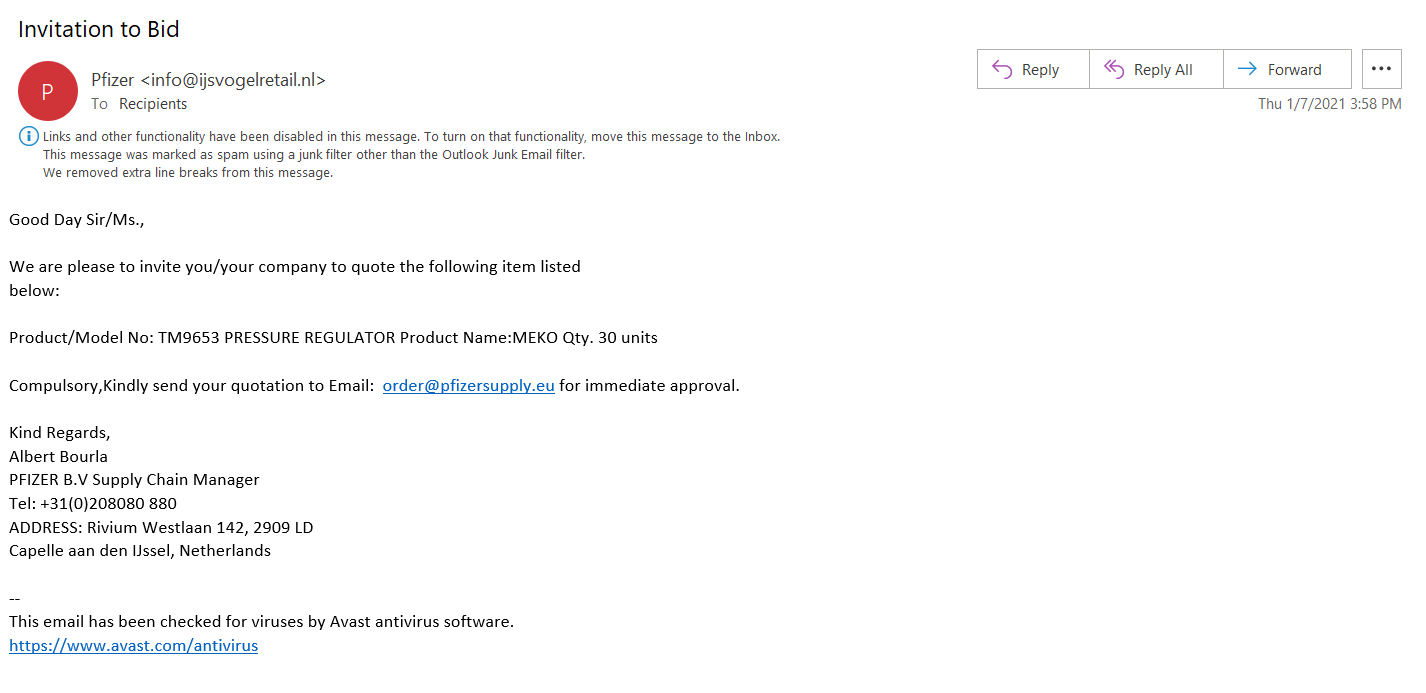
Phishing email example one.
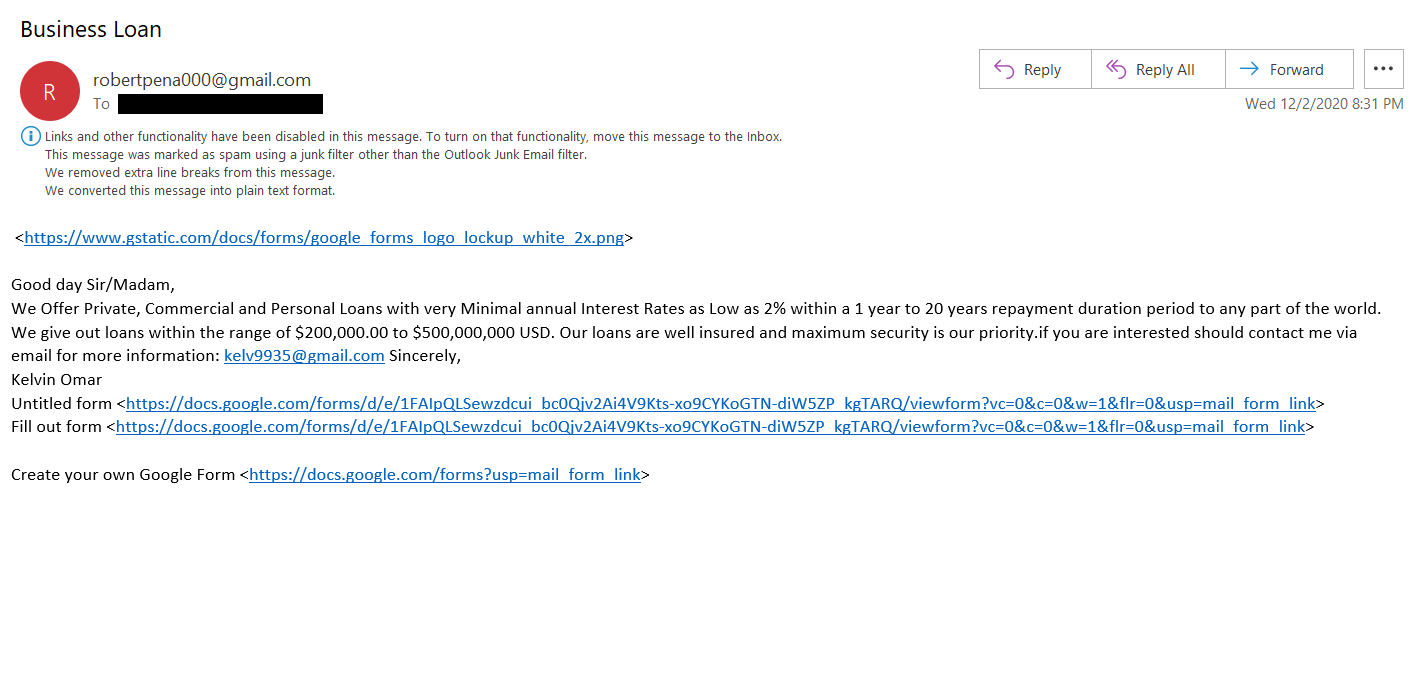
Phishing email example two.
In this first example, you’ll notice that the sender’s display name (Pfizer) and the email address itself don’t match. If the email was from Pfizer, it would come from an email address that matches the company’s domain and not an unknown website like “ijsvogelretail.nl.” The second example email is all over the place. It’s sent from the email address robertpena000@gmail.com, but the message says it’s from “Kelvin Omar” and tries to direct you to respond to a completely separate email address.
Needless to say, no legitimate business would ever send emails like this. Also, if the email was legitimate, it would address you by your name. Not “Sir/Ms.,” “Sir/Madame,” or any other generic form of greeting.
Tips for Using Email Safely (How to See If an Email is Legit)
In general, no one should open emails from people they don’t know. This is especially true for kids and teenagers. However, we understand that curiosity sometimes gets the best of us and people will wind up clicking on emails from unknown senders anyhow. So, whenever your kids and teens receive an email, remind them to take a few moments to check the following to see if it’s legitimate:
- Ensure the sender’s display name and email address match. This is the biggest red flag to call your attention. If it doesn’t match, mark it as junk and block the sender.
- Make sure the email address itself is accurate and isn’t slightly off. For example, emails from Amazon should come from addresses ending in “amazon.com” and not “amzon.com.”
- Read into the language of the message. Does any of it seem urgent or like it’s pushing you to take immediate action? Teach your kids and teens that if an email seems very demanding or urgent to bring it to your attention.
- Double-check the links. Before you click on a link in an email, be sure to hover your mouse over it first to ensure it’s legitimate. This will allow the true website link to display as an overlay.
- Avoid unusual attachments. If you receive an attachment you didn’t ask for, don’t open it. This is especially true for password-protected files. It’s likely malicious and will infect your device.
- Does the content make sense? Remind your kids to ask themselves, from a logic standpoint, if the message makes sense. Did they apply for a specific scholarship? Why would a coach or teacher send them an email asking for their login information?
If they receive an email that they realize is fake or a scam, it’s important that they flag the message as spam/junk mail and block the sender immediately.
Verify an Organization’s Digital Signature
Businesses and individuals alike can digitally sign and encrypt emails if they have the right tools at their disposal. This tool, known as an email signing certificate, adds a digital signature (basically, a long string of random numbers) to an email that tells your email client (Outlook, Apple Mail, etc.) that it hasn’t been messed with since it was sent. Let’s consider the following email as an example.
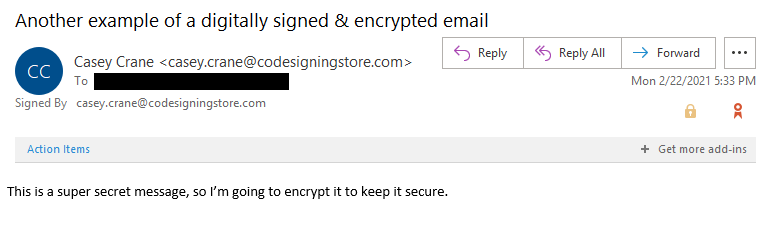
This email screenshot showcases the email’s digital signature badge and encryption padlock. This indicates
that the email has been digitally signed and secured via an encryption process.
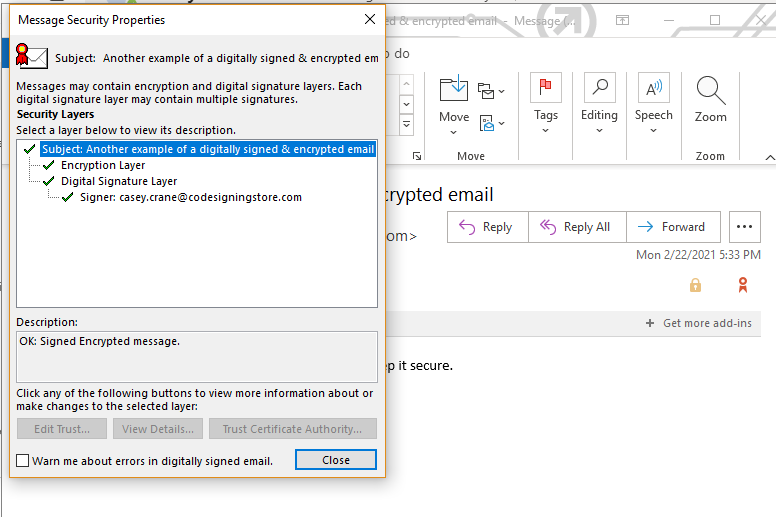
A screenshot of my email’s security-related information. It tells you that I signed the message using my official email address.
email’s security.
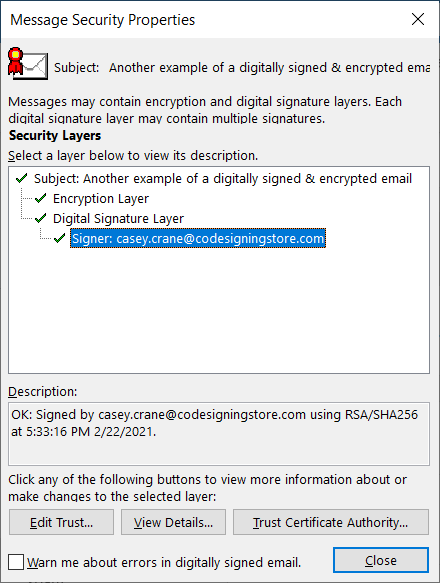
A screenshot of the message that my recipients see when I
send a digitally signed and encrypted email.
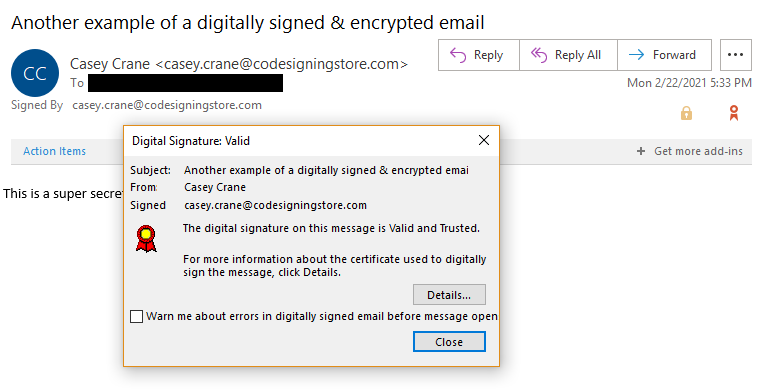
This last screenshot shows that the email has been digitally signed and is trusted by the email client (in this case, Outlook).
“How Using Social Media Affects Teenagers.” Child Mind Institute, 25 Jan. 2023, https://childmind.org/article/how-using-social-media-affects-teenagers/.
What Is Phishing?
Phishing occurs when a person sends a fake text, email, or pop-up message to get people to share their personal information, passwords, or financial information. Once they have this information, these criminals use the information gathered to commit identity theft or to steal money.
How to Recognize Phishing and Online Scams
When it comes to recognizing a phishing email or online scam, it takes practice and knowing what you are looking for. To start, remind yourself and your kids that legitimate organizations won’t call, email, or text to ask for your personal information, like a Social Security number, account number, or credit card number.
Maybe you and your colleagues have scrubbed up on the tell-tale sign of a phishing email, but are you able to spot these highly-sophisticated fraudulent emails? Let’s find out…
Here, we’ve given examples of some of the most popular and successful phishing emails out there. Take a look, share, and avoid…
1. The fake invoice scam
Let’s start with arguably the most popular phishing template out there – the fake invoice technique. Like many phishing attacks, this scam relies on fear and urgency, pressuring an end user to submit a payment for goods or services they’ve never even ordered or received.
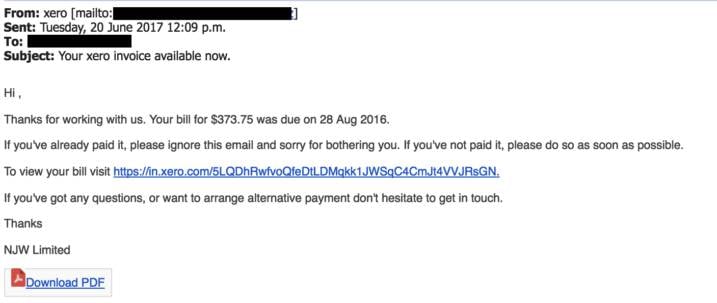
Finance departments are the obvious targets for this sort of attack, although there are plenty of potential victims that could be duped.
2. Email account upgrade scam
Faced with having your account expire unless immediate action is taken, the email account upgrade scam can appear to come from trusted email providers like Microsoft and Google, or simply from your company’s IT department.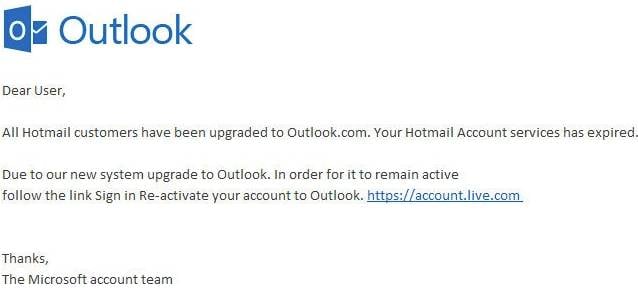
As you can see, nothing harmful stands out from this email. There are no stand-out grammatical errors, no elaborate requests, and the link itself would appear to direct to a safe “https” web page to an unsuspecting user. A useful tip is to hover over the link itself when being asked to give personal details – as the text itself often doesn’t represent the true destination of the link.
3. Google Docs scam
One of the most recent high-profile phishing techniques, the Google Docs scam offers an extra sinister twist as the sender can often appear to be someone you know.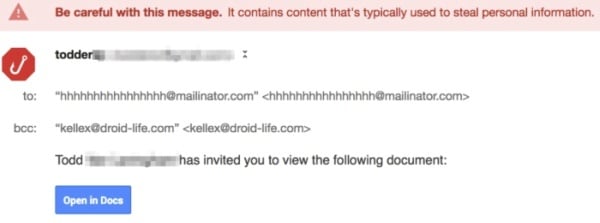
This ultra-sophisticated email encourages you to click on its link in order to view a ‘document’, which then takes you to an almost identical version of Gmail’s login page. Once an account has been selected, you’re then invited to grant access to your Google account, meaning the attacker has free rein.
4- Dropbox scam
The same old story of encouraging users to click a link, yet a whole new platform to utilise. Dropbox, the online sharing and storage platform, has grown massively in popularity over recent years – and so too have its fraudulent copycats.
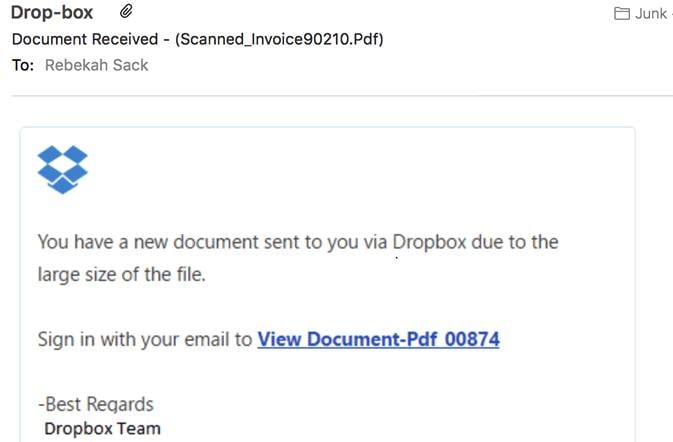
The Dropbox phishing email usually works by informing a user that the ‘file’ which has been emailed to them is too large, and needs to be opened with a quick “click on this link”. You’ve probably guessed by now that a fake Dropbox landing page is waiting… and you’d be right. What you might not have guessed is that this page can actually be located within Dropbox itself – waiting patiently to harvest your details.
Reference:
Gillis, Alexander S. “What Is Phishing? How It Works and How to Prevent It.” Security, TechTarget, 5 May 2020, https://www.techtarget.com/searchsecurity/definition/phishing.
How to Use Social Media and Chat Apps Safely
Social media and chat apps offer many benefits for kids and teenagers, including a way to keep in touch with friends and family who don’t live nearby. That’s why we’re going to lump them together. However, there are also risks that stem from social media usage, including:
- Exposure to inappropriate or illegal content
- Cyberbullying
- Cyberstalking
- Identity theft
- Phishing scams
- Financial scams
- Malicious ads and links that can install malware
There are plenty of online scams that target kids and teens. Some of the most common include:
- Fake postings about contests and free giveaways.
- Fake ads for free or inexpensive luxury goods.
- Messages about talent searches and modeling opportunities.
- Surveys that ask for seemingly unimportant private information.
- Grant, scholarship, and job opportunities.
- Messages that contain videos or images that are actually malicious (or direct to malicious sites).
Dangerous Apps Your Kids & Teens Should Avoid
Cronister says that some social apps are especially dangerous because they allow people to communicate without providing their personal information to register or saving any records of the conversations. While this is good from a user privacy perspective, it also makes it difficult for law enforcement to gather proof of any illegal activities involving children.
This can be anything from an adult sending a teen or child nude images to human trafficking-related communications. Because of this anonymity and lack of records, some of the potentially most dangerous apps include:
- Discord — What originally started as an app for gamers has morphed into something much bigger. Users can participate in group or direct messages. Although this app does have some privacy and safety settings, there are no parental control settings you can use.
- MeetMe — The point of this app is to create a profile of yourself with the ultimate goal of physically meeting up with someone.
- Snapchat — This messaging service allows users to exchange text messages, photos, and videos that will self-destruct automatically after a set amount of time.
- Telegram — This is another app that allows users to set expiration dates for messages they send. Once a recipient opens a message, it starts a countdown that indicates how long the message will remain before it destructs. While this option isn’t set by default, users can manually enable it.
- WhatsApp — This app chat app now allows users to share disappearing messages that will self-destruct as well.
- Whisper — This anonymous social networking app aims to create as much anonymity as possible by showing little to no identifying information (although it does show a geographic location). While this anonymity may sound good in terms of privacy, it could lead to situations to people posting inappropriate or threatening content that your kids and teens may see and having no way for you or law enforcement to identify the sender. It’s also been used by predators to lure kids for sex.
Facebook, which also owns Instagram, reports that in Q3 2020, 0.05%
of content violated their child nudity and sexual exploitation of children
policy on that platform.
Fake or Duplicate Profiles Are a Big Problem
But just how big of a problem are fake profiles? Let’s just consider the issue on Facebook to give you a little perspective.
Facebook reported in their U.S. Securities and Exchange Commission (SEC) filings report on Jan. 28, 2021 that 11% of their global monthly active users, or MAUs, in Q4 2020 were duplicate accounts. (Meaning that someone created a fake duplicate profile of real people, likely to try to dupe other people.) Considering that the company reports there being “2.797 million” (2.79 billion) active monthly users in December 2020 alone, that equates to roughly 307 million MAUsactive fake profiles.
Facebook also reports on their Transparency site that “fake accounts represented approximately 5% of our worldwide monthly active users (MAU) on Facebook during Q4 2020.” While this may not sound like a lot, but let’s remember that Facebook reports having more than 2.7 billion MAUs. This means that on Facebook (and Facebook messenger) alone, 16% of their accounts are either fakes or duplicates.
Facebook, which also owns Instagram, reports that in Q3 2020, 0.05% of content violated their child nudity and sexual exploitation of children policy on that platform. Basically, this equates to about five out of every 10,000 views containing that type of inappropriate material or content.
So, millions of fake user profiles are on chat and social platforms, and many of those people are up to no good. Here’s how you can find out who you’re really interacting with online.
Learn to Identify Fake & Duplicate Profiles
Fake profiles are a big problem on social media. People create profiles for people who don’t exist — often using stock images or stealing private individuals’ images that they gather through Google Images and other sources — to try to scam or blackmail people.
But how can you tell whether a profile is fake or duplicate?
- You don’t personally know the requester. If you don’t know someone, there’s no legitimate reason for them to try to connect with you.
- They aren’t friends with anyone you know. This concern goes hand-in-hand with the last point.
- You’re already friends with the requestor on a different account. Duplicate profiles are commonplace and involve someone creating a doppelganger profile with the hope that you’ll not realize you already have them on your network.
- The requestor uses poor grammar and spelling. This is often a big giveaway for scammers, many of whom aren’t native English speakers.
- The profile was created recently and contains limited or no information. Cybercriminals often don’t put a lot of effort into creating fake profiles because they know that they’ll have short lifespans. They rush to put profiles together to use for a short period.
- The profile’s images are all recent or limited. This goes along with the last talking point. If the profile has limited or multiple images that have recently been added prior to friend requesting you, it’s a big red flag.
- The requestor asks you to do something with a sense of urgency. Using language that evokes a sense of curiosity, fear, or panic is a tactic cybercriminals use to manipulate victims into doing what they want.
- The location of the person is overseas. A common scam (known as relationship fraud) involves a bad guy pretending to be a doctor or a soldier who is working or serving overseas. (You’ll see a perfect example of that momentarily.)
- A reverse search on Google shows other profiles using the image. Often with fake profiles, if you use Google’s reverse image search tool to check an image, you’ll see that the image has been used elsewhere online, especially on other profiles.
- The person’s social media activity takes place in odd hours for someone from that region. Say, someone says they live in Savannah, GA but all of their profile updates occur between 2 a.m. and 4 a.m. EST. This may indicate that the person doesn’t really live in Savannah.
Here is one such example of a fake profile:
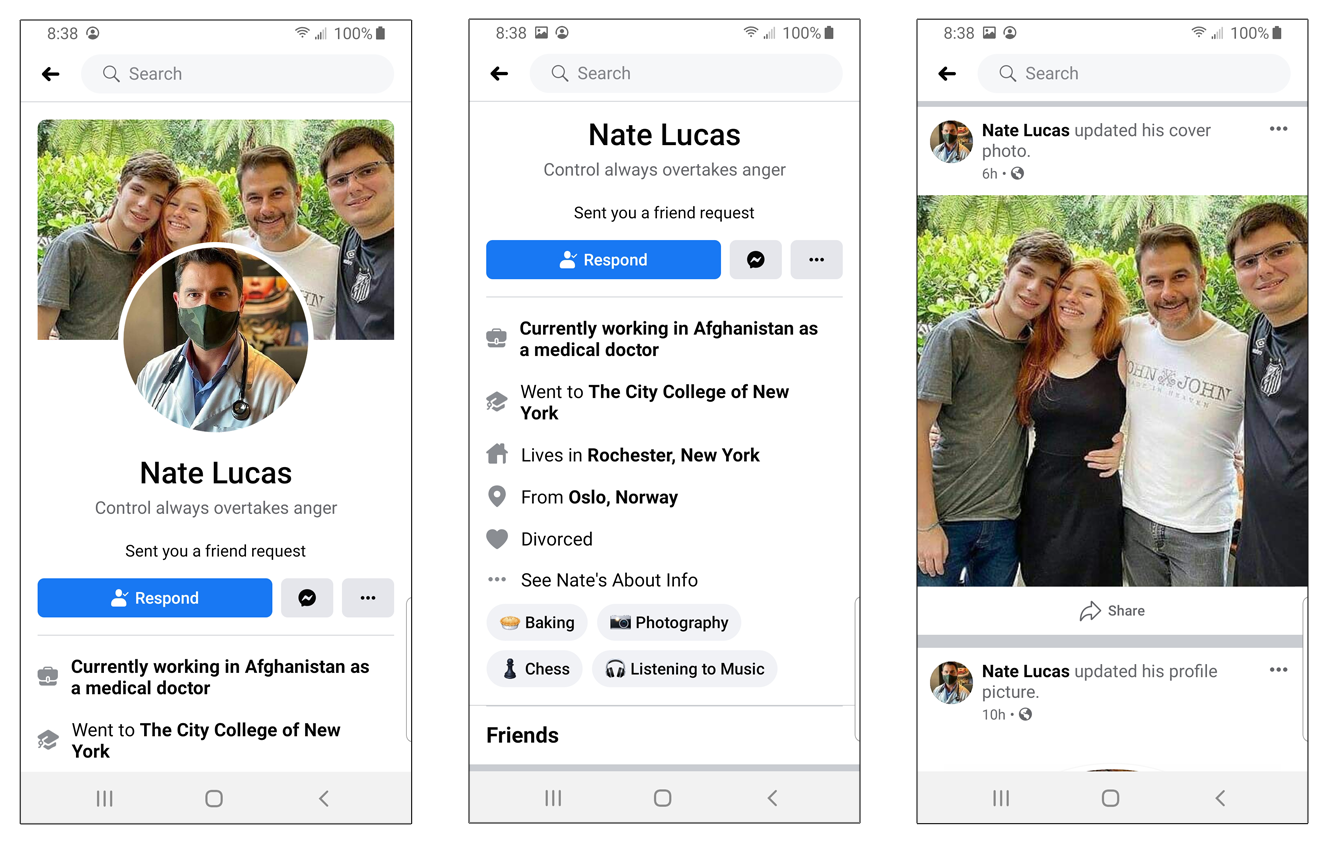
This three-part screenshot shows the basic information of a fake Facebook profile that was recently created.
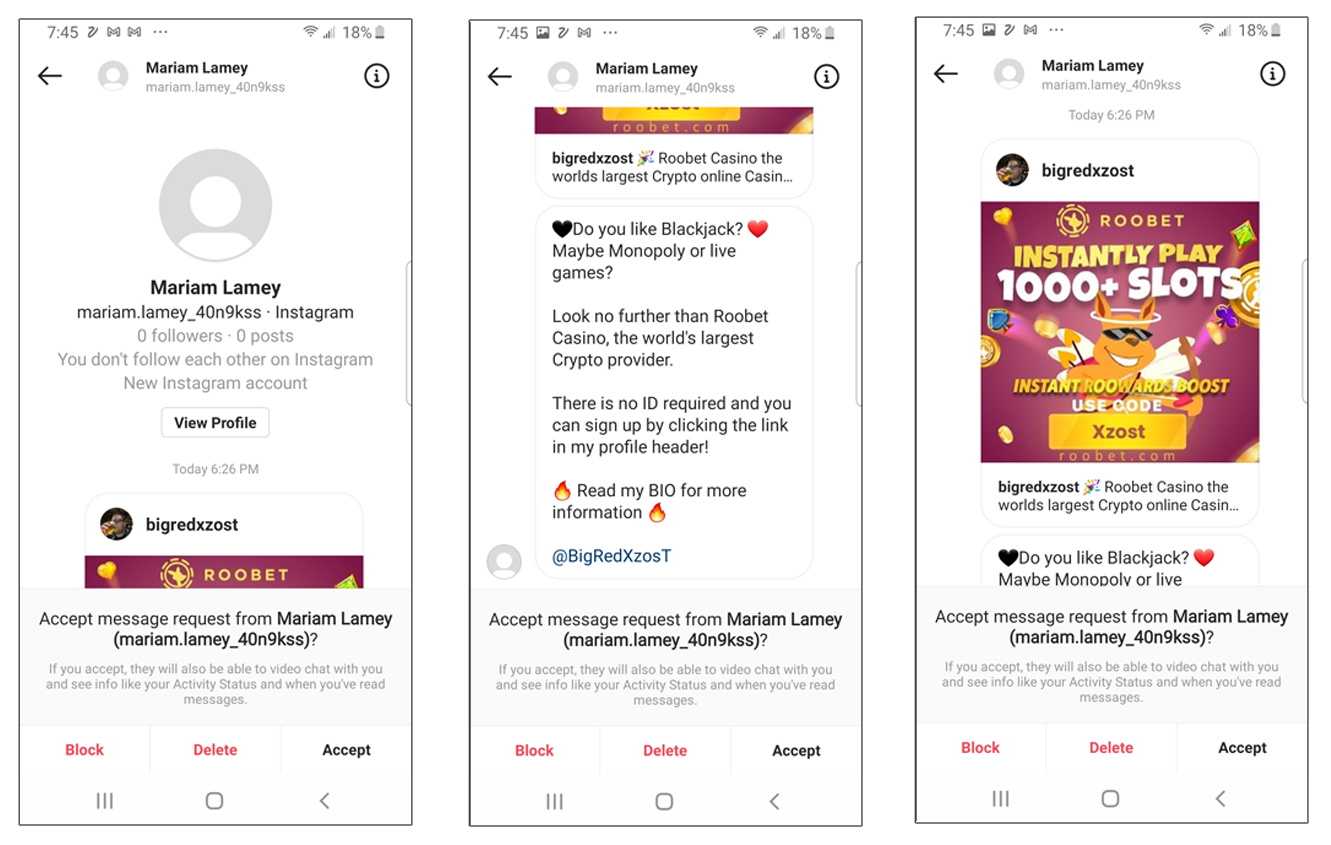
This set of screenshots showcase serves as an example of a fake spam bot profile.
In the example above, you’ll see an unsolicited private message from someone that the recipient isn’t connected with who has no followers or posts. The message itself appears to be spam. However, it may contain a malicious link that could auto-download and install malicious software onto the recipient’s mobile device.
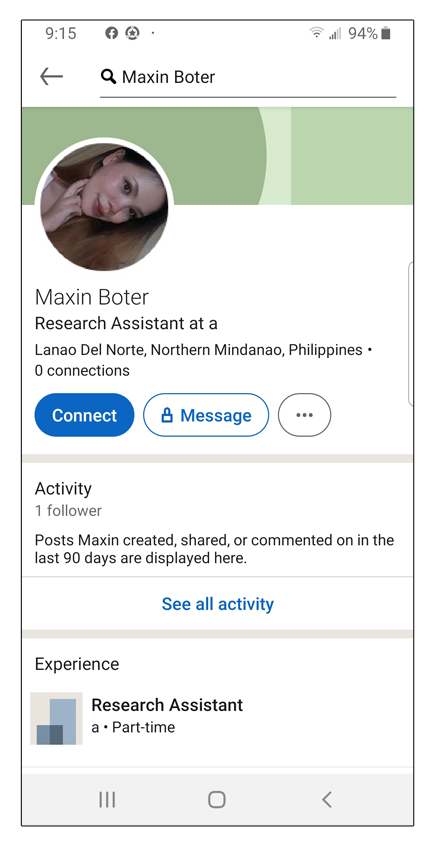
Here’s an example of a fake LinkedIn profile that requested a connection with one of our employees. Notice how the profile has no friends and no real information. This is an indication that the profile is likely fake. Another way to tell is if they have many people they’re following but no connections of their own. This type of profile could be used to gain access to profiles that are set to private for information-gathering purposes.
If you still aren’t sure whether the person you’re talking to is real, another method Cronister recommends is asking them to take a specific picture of themselves doing something. The image would need to be of them doing something specific — ideally, something that’s unusual or silly — or writing a specific unique word on a piece of paper. This prevents the person from using a stock image or an old photo because they’d have to do something specific at that moment.
But what should your kids do when they receive messages from unknown or potentially fake users? A good rule of safety is to think in terms of “stranger danger” for kids — never talk to strangers. This counts in both offline and online environments. So, what they should do is report any suspicious profiles to the platform (Facebook, Snapchat, etc.) and block ‘em!
Limit the Information They Share on Social Media
This is a big one. Kids and teens are often more open and trusting — or, in some cases, overly confident. This may make them more liberal and open in terms of sharing their personal information online. This is a dangerous mindset, Cronister warns:
“Most offenders are crafty enough to ‘friend’ or ‘follow’ children for long enough that the child becomes comfortable before attempting to victimize or groom them. They are oftentimes posing as kids themselves.”
Some other app privacy settings and considerations include:
- Setting their profiles to private to limit access to their images and information to only their network.
- Checking each social platform’s security settings and disabling unnecessary permissions.
- Not allowing other apps or platforms to connect to your kids’ or teens’ social media profiles.
- Reminding kids to not complete or publish surveys that ask for private information.
Reference:
“Best Messaging Apps and Websites for Students, Teachers, and Parents.” Common Sense Education, https://www.commonsense.org/education/lists/best-messaging-apps-and-websites-for-students-teachers-and-parents.
•Who uses email in the class?
• Have you ever been scammed via email? Why did you think it was a scam?
• Who has an account on a social network, including but not limited to, Google+,
Facebook, Instagram, Tumblr?
• Is it safe to use your real personal information for an online character? Why?
• How can you get an email scam from someone if you never gave your email address to
that person?
• Can scams happen on websites that you visit?
• If you get a chain letter saying that something bad will happen to you or to someone you
know if you don’t forward it, should you go ahead and forward it to all your friends?
Activity 1:
Click here–>>
Click this link: My App
- Follow the “Detecting Phishing Email” track
- If you finish early, try the “Password Management” track
- 2 awesome games to learn more about phishing
- Fun, interactive “fishing” learning game: http://bit.ly/2raTTz6
- Detecting between scams and real emails: https://www.opendns.com/phishing-quiz/
- Check out an incident at my high school! http://bit.ly/2rJDIFZ
- Make Your Own App teaching your family and loved ones about phishing attacks:
- Thinking points: What can we do to avoid them? How do we know that an email is a phish? Should we click the link?
- Go to https://studio.code.org/ and scroll down to the bottom where it says “Projects.” Click “Make an App Lab App.”
Activity 2:
https://mailheader.org/ website for analyzing message headers. Again simply paste the header information into the field provided and you get a nice, graphical report out of it. Simply go over your gmail inbox click three dots and go “show original: copy and paste your header to mailheader.com.
:max_bytes(150000):strip_icc()/002-how-to-see-full-email-headers-in-gmail-1171960-bcfa0d49ed934a07a2e38b0d8395d9db.jpg)